Configuration errors can block a user's access to S3 data when connecting through the Cyral S3 Browser. Below, we explain how to diagnose and fix the most common misconfigurations.
Observed behavior
The problems we describe here assume that the Cyral administrator has successfully configured the S3 Browser so that a user of the configured IAM role can connect to the desired S3 resources through the S3 Browser. The problem arises when other users are unable to connect, even though their user accounts are mapped to the correct IAM role.
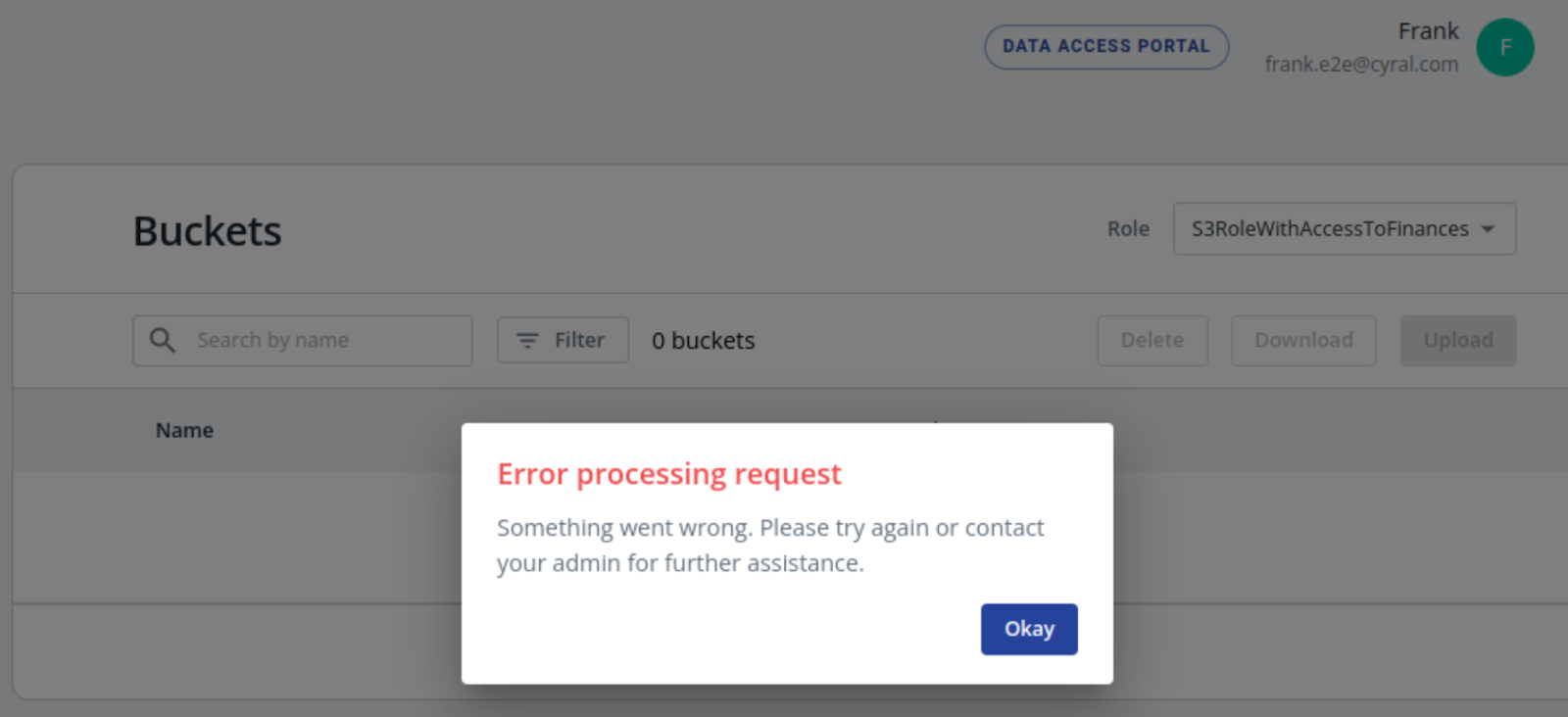
The S3 browser reports an error similar to this one:
Assumptions
We assume the administrator has correctly configured:
In these instructions, we assume that no Cyral policies are in place for the users. If you do have policies in place, check the rules that apply to the user in question.
Reproduce the problem
With the user account that you know to be correctly configured, make sure you can still connect to the S3 resources through the Cyral S3 Browser.
With the user account that is having trouble, attempt to connect. A failed attempt will often look like the image below, with no buckets shown in the S3 Browser.
Troubleshooting procedures
Check the identity map
Double-check the identity map section for the S3 repo (Ask your SSO administrator if the mapping is correct, or see Map an SSO user or group to an IAM Role):
If the identity map is wrong (for example, if the connecting user's username or group is not mapped to the right IAM role), fix it and try to reproduce the problem again.
If the identity map is correct, check the connectivity between the user's computer and the sidecar.
Check the user's connectivity
Check if the affected user can reach the sidecar. Ask the user to copy the sidecar endpoint and port number, in the format: https://sidecar-endpoint.com:1234. Have the user paste this into their web browser's address bar, and hit enter.
If the page fails to load, due to timeout or being unreachable, it's likely that the sidecar endpoint can only be accessed by users connected to a specific VPN. Recommended steps:
Have the user double-check that the required corporate VPN configuration (if any) is in place.
Have them check whether their web browser has proxy configuration settings that interfere with the sidecar connection.
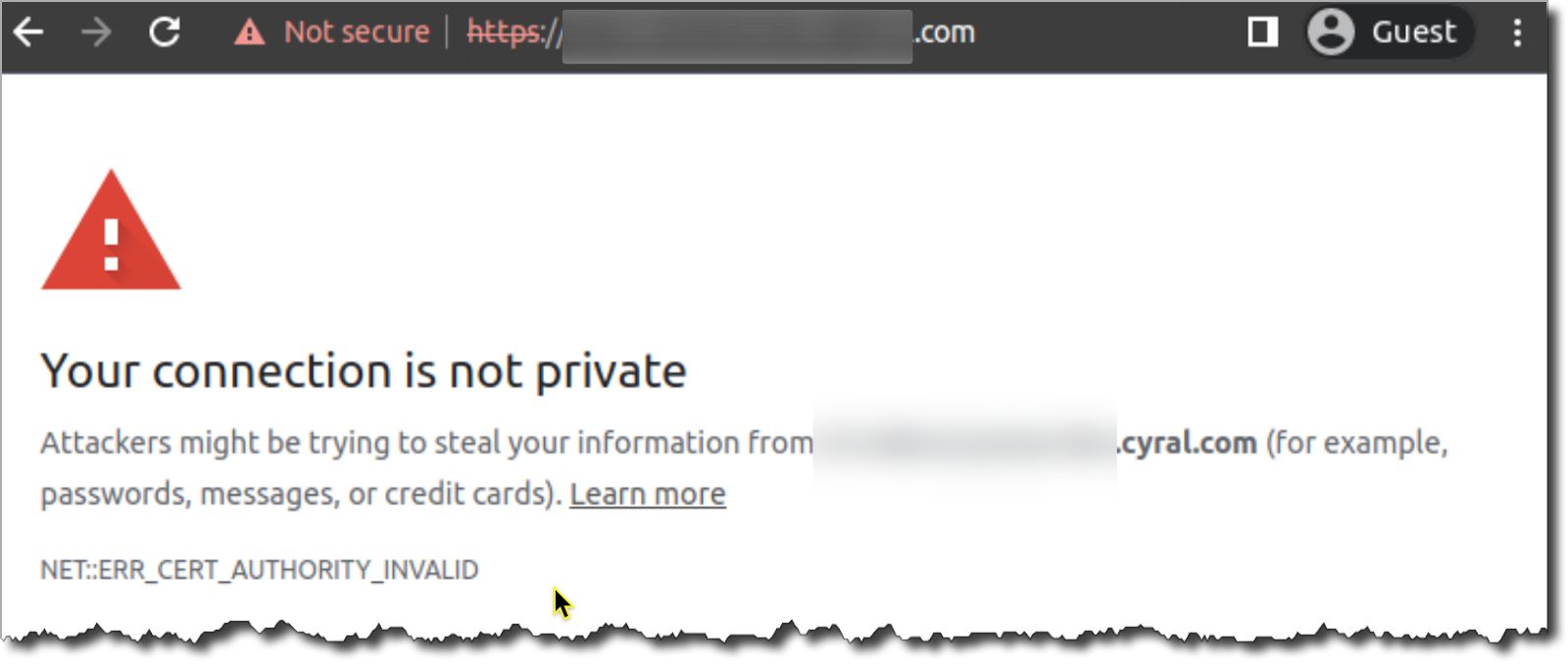
If the page loads but shows a warning message about privacy settings, similar to the reference image below, it means the client browser does not trust the certificate used by the sidecar. This usually happens when the S3 Browser/sidecar was configured with a self-signed TLS certificate (usually generated by your organization), instead of a certificate generated by a known certificate authority like DigiCert, GoDaddy, or Amazon.
Recommended step: You or your security team should provide the required TLS certificate chain to the affected user¹. The affected user must configure either the operating system or the web browser to accept and trust this certificate chain. See "Provide the TLS certificate chain to your users," below.
Alternative, temporary step: Have the affected user open the Advanced options in their web browser and choose to ignore the warning and proceed to the (in)secure website. Chrome, Firefox, and Safari provide this option.
¹: When a company issues and configures the S3 Browser/sidecar with their own self-signed certificates, every user that intends to use the browser has to install them.
Provide the TLS certificate chain to your users
The steps for installing the TLS certificate chain depend on the user's operating system and browser. The following instructions show the most common steps: